If you have ever configured a browser to “use a proxy” or wondered why the office network routes everything through a mysterious gateway, you have brushed up against an HTTP proxy. This middleman is everywhere: in corporate firewalls, public Wi-Fi hotspots, parental-control tools, and even data-saving modes on mobile phones.
Yet most people have only a vague idea of what an HTTP proxy actually does or why it matters. In this guide, we’ll unpack the full HTTP proxy meaning, explore how an HTTP proxy operates, and show where it shines and where it doesn’t. By the end, you’ll know exactly how to tweak your proxy settings for faster and safer browsing.
What is an HTTP proxy?
At its core, an HTTP proxy is a specialized proxy server that lives at the application layer of the OSI model and speaks one language: HTTP (and, by extension, HTTPS).
The official definition in RFC 9110 describes an HTTP proxy as “a message-forwarding agent that acts on behalf of either the user agent or origin server.” In simpler terms, it is a forward proxy that impersonates the client when talking to websites, making and receiving HTTP requests on the user’s behalf.
Because an HTTP proxy server lives between the client and the destination, every byte passes through it. This vantage point lets administrators rewrite headers, filter web content, inject authentication challenges, or cache static objects for lightning-fast delivery.
A typical HTTP proxy listens on port 8080 or 3128 and can be deployed as software, a hardware appliance, or a cloud service. Whatever the form factor, the defining trait remains: it intercepts traffic, speaks HTTP, and exposes only its own IP address to the outside world.
Key characteristics
- Application-layer awareness: An HTTP proxy parses each header to make policy decisions.
- Request & response interception: The proxy server can compress images, strip ads, or block trackers before forwarding the page.
- Caching & content adaptation: Popular assets are served locally, accelerating web browsers across the network.
- Identity masking: Sites see only the IP address of the HTTP proxy, never the user’s.
- Multiple deployment modes: Transparent, explicit, or reverse proxying, depending on proxy settings and network layout.
How does an HTTP proxy work?
So, how does an HTTP proxy work under the hood? Picture a relay race for data:
1. The client sends a request to the proxy
Your browser directs ordinary HTTP requests to http://proxy.example.com:8080, the address stored in system-wide proxy settings.
2. The proxy evaluates the request
Acting as a forward proxy, the device checks user credentials, filters URLs, scans for malware, and consults its cache.
3. The proxy forwards the request
If the asset is not cached, the HTTP proxy server opens an outbound TCP session and forwards the request. The destination sees only the proxy’s public IP address.
4. The server responds to the proxy
The origin site returns HTML, images, and scripts. Because the TCP handshake terminates at the proxy, upstream jitter or throttling never reaches the client directly.
5. The proxy transforms and relays the response
The HTTP proxy can resize images, inject disclaimers, gzip files, or quarantine suspicious payloads before sending the page to the browser.
Repeat this loop millions of times per hour, and you have a production-grade HTTP proxy cluster that keeps thousands of users safe and productive.
Benefits and limitations of HTTP proxies
Benefits of HTTP proxies
Deploying an HTTP proxy (or any enterprise-grade HTTP proxy server) delivers four big wins:
- Privacy & anonymity: By cloaking the client’s real IP address, a forward proxy thwarts targeted ads and invasive profiling.
- Access control: URL blacklists, category filtering, and time-of-day rules are enforced in one place: the proxy server.
- Bandwidth optimization: Caching heavy web content (software updates, images, libraries) slashes WAN usage and speeds up web traffic.
- Monitoring & logging: Centralized logs feed SIEM tools, revealing anomalies and bolstering security measures such as data-loss prevention.
Limitations of HTTP proxies
Even a well-tuned HTTP proxy has drawbacks:
- Protocol limitations: A vanilla HTTP proxy only understands HTTP/S. Streaming or VoIP traffic will time out; you’ll need a SOCKS-based forward proxy for those.
- Latency overhead: Deep packet inspection and caching add extra hops, which can sometimes frustrate real-time apps.
- Security weak points: A poorly secured proxy server becomes a man-in-the-middle. Enforce TLS everywhere and keep patches current.
- Scaling challenges: Decrypting massive HTTPS streams demands serious CPU; vertical scaling gets expensive fast.
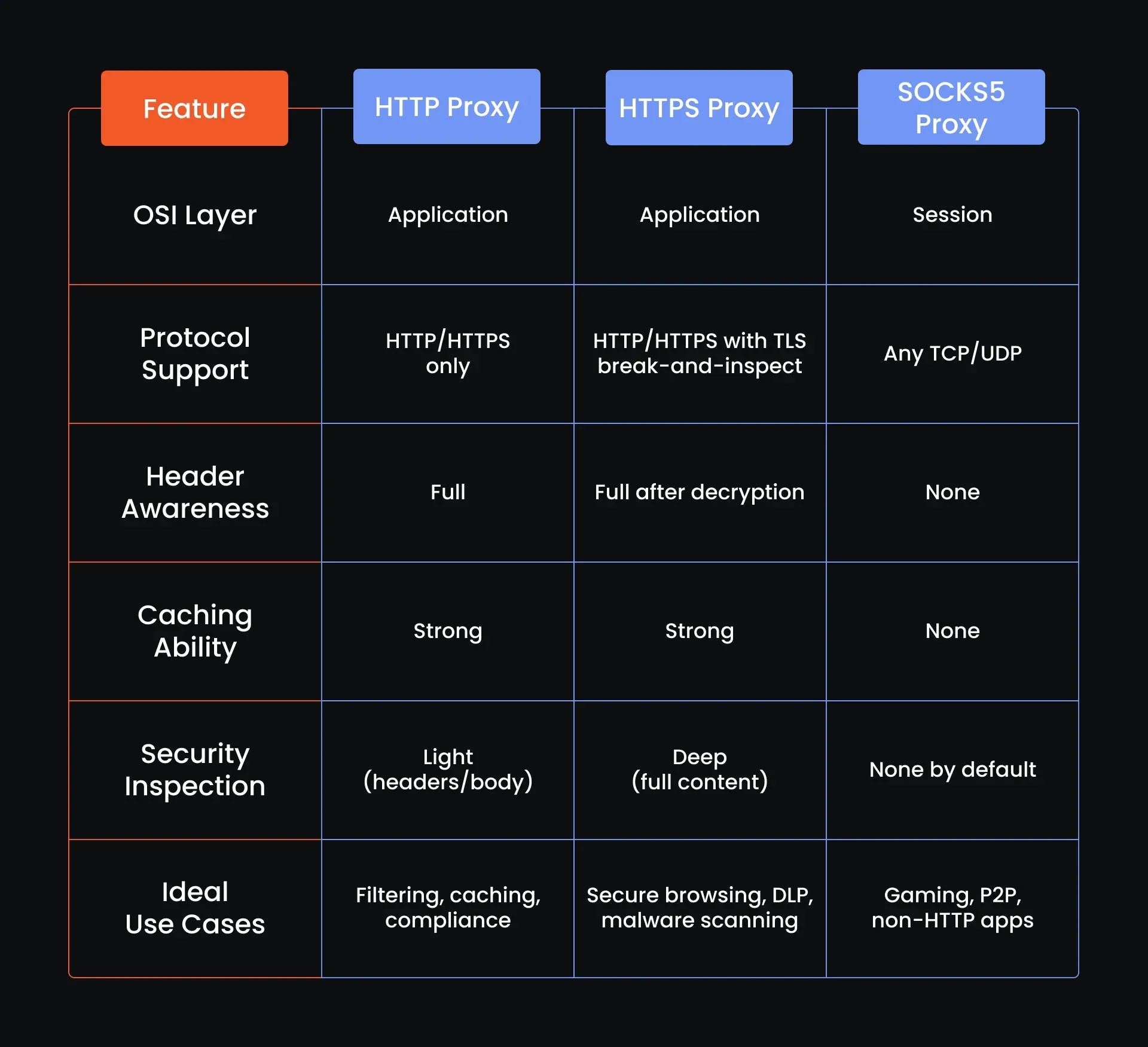
HTTP proxy vs. other proxy types
HTTP vs. HTTPS proxy
In the proxy universe, HTTPS is essentially HTTP proxy plus SSL/TLS termination. The HTTPS variant decrypts secure sessions, inspects payloads, and then re-encrypts content before forwarding.
That deep-inspection capability makes it indispensable for regulated industries.
By contrast, a classic HTTP proxy passes encrypted streams untouched: more private, but blind to hidden threats.
HTTP vs. SOCKS proxy
A SOCKS proxy works one layer lower, forwarding raw TCP or UDP packets. That flexibility covers FTP, SMTP, P2P, and chat protocols. The trade-off: a SOCKS proxy cannot read or cache web content nor block phishing URLs.
If your goal is to shape web traffic from modern web browsers, choose an HTTP proxy; if you need broad protocol coverage, pick SOCKS.
Comparison table
Real-world use cases for HTTP proxies
- Academic research & competitive intelligence: Crawlers rotate through a pool of HTTP proxy nodes, each with a unique IP address, to bypass rate limits while gathering web content.
- Mobile-data compression: Some carriers route all data through an HTTP proxy farm that compresses images and minifies scripts, reducing customer bills and backbone load.
- Regulatory filtering in schools: Districts rely on a central proxy server to block adult sites. Teachers authenticate to the same forward proxy but receive looser policies.
- Enterprise SaaS access: Corporations deploy a high-availability HTTP proxy server cluster that enforces CASB rules, tokenizes sensitive data, and scans every file for malware.
- IoT fleet management: Millions of smart-home sensors phone home through a lightweight HTTP proxy, allowing vendors to update firmware and shape web traffic without exposing each device.
Across these scenarios, control is the common thread. A strategically placed HTTP proxy hands administrators the steering wheel for privacy, visibility, and performance, often at a fraction of the cost of more exotic solutions.
Pro tips for deploying an HTTP proxy
- Size the hardware carefully. A busy HTTP proxy cluster needs a CPU for TLS and SSDs for cache.
- Segment management traffic. Never expose the admin console of an HTTP proxy to the internet.
- Automate policy updates. Tie HTTP proxy rules to CI/CD, so blocking a domain is a pull request away.
- Monitor certificate validity. An expired cert on an HTTP proxy breaks every secure site.
- Plan for redundancy. Health checks ensure another HTTP proxy takes over instantly if one fails.
- Document proxy settings. Users need a clear path when the HTTP proxy mistakenly blocks legitimate web content.
Ways to go?
Want hands-on experience? Open-source projects like Squid and Traefik let you turn a Raspberry Pi into a fully featured HTTP proxy server. Cloud marketplaces also offer images that drop an HTTP proxy server into your VPC in minutes, complete with dashboards and autoscaling.
Also, if you do need a sure-fire solution, go for a reliable proxy provider, like MarsProxies. Our proxies all have support for HTTP/HTTPS (and SOCKS5, for that matter), and the number of our residential proxies is deliciously large!
Conclusion
Remember this: the phrase HTTP proxy meaning boils down to “an intermediary that speaks HTTP for you.” And when colleagues ask, “How does HTTP proxy work in our stack?” you can now walk them through the full request lifecycle with confidence.
By standing in the middle of every HTTP request’s path, a well-configured proxy server offers fine-grained command over web traffic, hides your true IP address, applies robust security measures, and accelerates browsing through smart caching.
Yes, a single HTTP proxy server won’t handle non-HTTP protocols or eliminate latency entirely, but for most organizations and privacy-minded individuals, it remains the simplest, most effective way to reclaim control of the open web.
Want to dive deeper and learn even more? Don't hesitate to check out our Discord. It's filled to the brim with like-minded individuals.