The internet is, essentially, a huge network of connected devices. But if you study its structure more closely, you will notice its breakdown into much smaller segments called subnets. Subnets allow more efficient and secure device communication but also introduce additional routing challenges.
One of them is locating the correct subnet address out of hundreds of thousands of computer networks that make up the internet. That's where subnet ID jumps in. This identifier allows for establishing the best data routing path to the correct subnet for easier network management.
Simultaneously, smaller networks are safer cybersecurity-wise. A network administrator can easily check a subnet backlog for issues without wasting time analyzing the whole massive structure, which is essential for corporate workplace security. Additionally, it's much easier to allocate and manage host IP addresses on a fragmented subnet.
In this article, we will explain what subnet ID is and provide a simple guide on how to calculate it at the very end.
Understanding the Subnet ID
A subnet ID, sometimes also called network ID, is a unique identifier that marks a smaller network location within a larger one. Whenever routers receive data packets, they can derive this identifier from the recipient's IP address and send the data to the correct location.
It works similarly to worldwide postal services. For example, you want to send a letter from Germany to Boston. Whenever your local postal office receives the shipment, they inspect the recipient's address. They notice it’s in Massachusetts, the US state. Instead of searching for the physical recipient's address, they forward it to the local post office, which works similarly to the subnet routing.
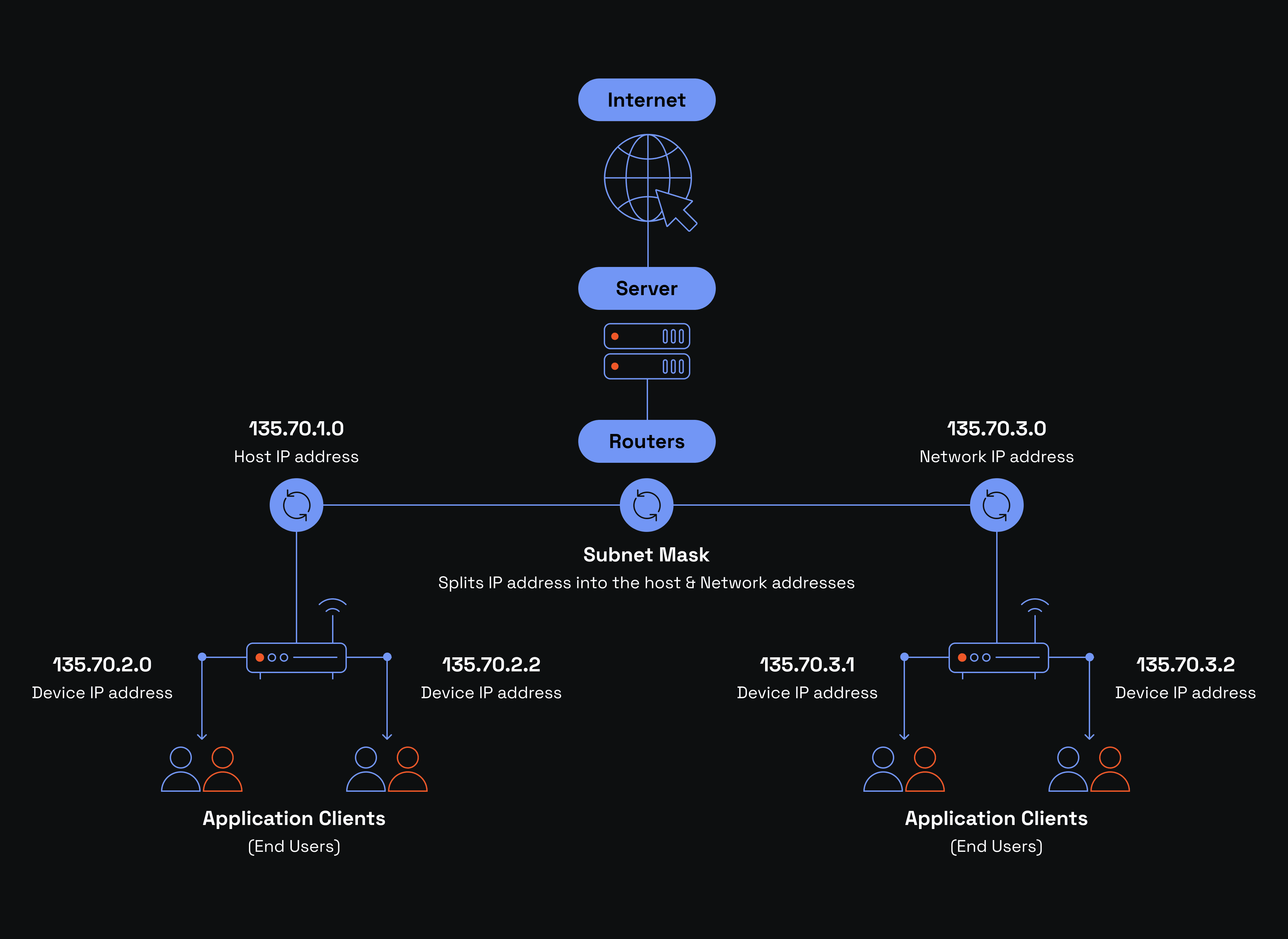
How exactly does it improve network addressing? Without contacting the local Boston postal office, the one in Germany should then send the shipment directly to the recipient's physical address. Because the German postal office does not operate in Boston, the routing becomes highly complicated. Instead, they contact the local post office (subnet ID), which has all the required recipient information for a speedy delivery.
IP addresses play a crucial role in this routing logic. Let's take a random IP address of 240.172.47.119. Whenever a router accepts a data packet destined to this IP address, it derives the network prefix to identify which subnet it belongs to. It then routes the data to the correct local network according to routing protocols. Lastly, once it reaches the target network address, local routers identify the host ID part and forward data to the end destination.
Why Subnet IDs Matter in Networking
Subnets are essential for the vast majority of enterprise networks as well as the overall structure of the World Wide Web. Firstly, segmenting larger networks into smaller parts allows for easier management.
Network Management Optimization
Whenever you divide a large computer network into smaller parts, you can set up monitoring to inspect all activities on it. This way, your backlog will show only relevant information to a particular subnet instead of displaying all network events and errors.
The same logic is widely used in many problem-solving situations when a bigger problem is divided into small segments to be solved one by one. Whenever there's a network traffic issue, a subnet ID allows network administrators to focus on a smaller network portion to identify the problem instead of wasting time and energy analyzing the whole network perimeter.
IP address Allocation
Another crucial benefit is to allocate IP addresses within a local network efficiently. Currently, IPv4 is the most widely used IP address type. There are also newer IPv6 IP addresses, which use letters alongside numbers to create a large address space, but we will focus on IPv4 as it is still the primary tool to route data packets to the correct network address.
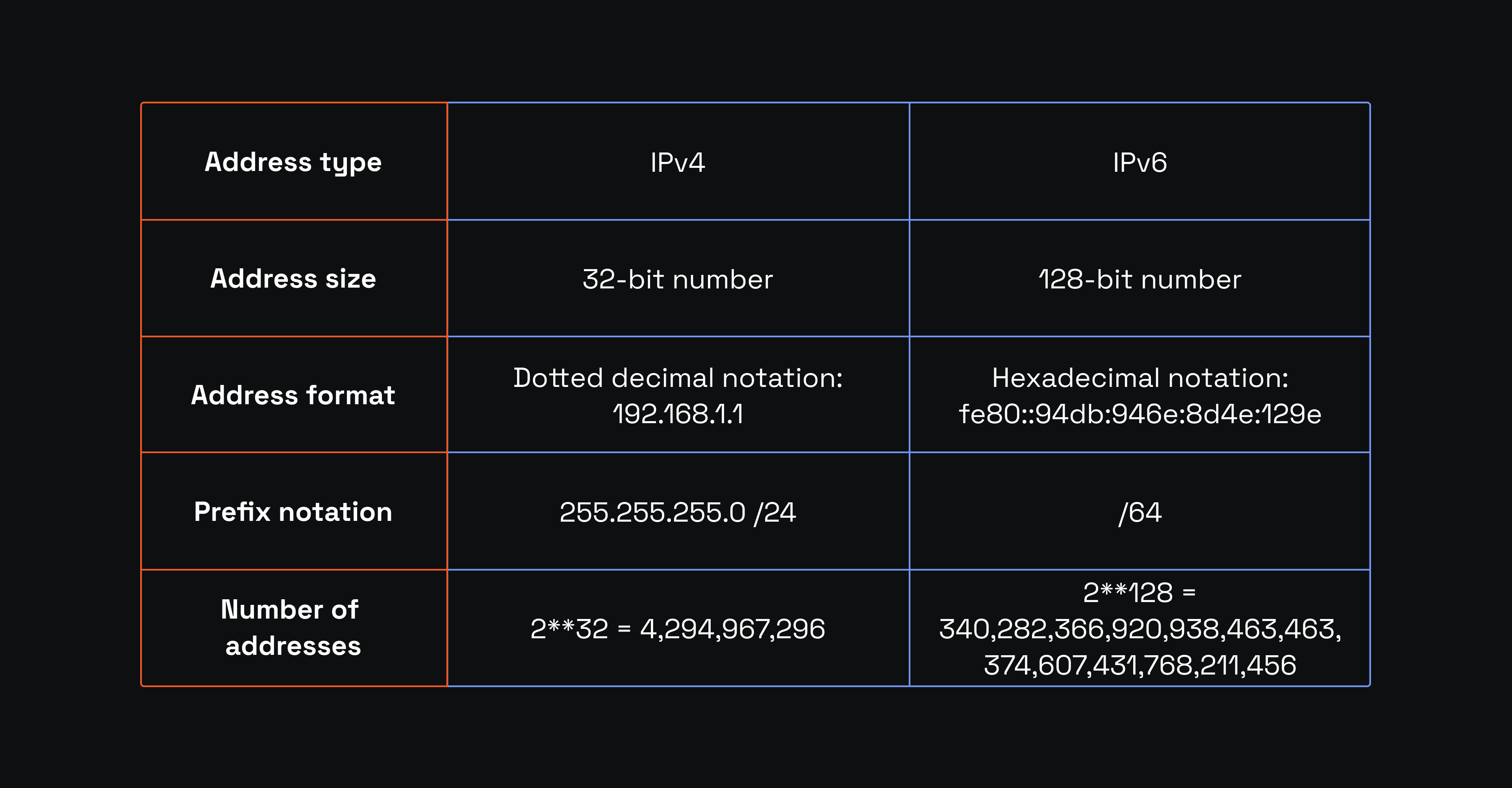
As you can see, both types offer limited IP addresses that are gradually running out due to the increasing number of internet-connected devices. Simultaneously, billions of online devices create a huge routing challenge. A subnet ID allows the organizing of IP addresses within a smaller network to optimize network traffic and delivery speed.
Efficient Data Routing
This brings us to another essential benefit. A subnet identifier helps avoid network congestion when too much data is routed through the same devices, resulting in a router or server overload and an internet speed dropdown.
For example, a business has offices in France, the UK, and Canada with 100 devices in each country. The best way to organize it is to create three subnets that would connect its 100 devices in a network. Whenever a person wants to send data, the router marks down the subnet identifier and forwards it to the correct country. Upon arrival, the host ID sends the data through the most optimal route to the target recipient.
Web Scraping
Although indirectly, understanding subnet identifiers can help you to scrape the web. Generally, web scraping requires reliable residential proxies with an excellent IP reputation. This way, scraper bots can rotate IPs to send multiple data request queries to avoid detection and IP bans.
However, whenever a website identifies scrapers, it often blocks access to the whole subnet. This way, even if you switch to another proxy server, it will still be banned if it belongs to the same subnet. You can use the practical steps in this article to identify available proxy subnets and prevent reusing them to increase scraping success rates.
Cybersecurity
Last but not least is the network security. Smaller subnets are much easier to monitor and in case of a cyber attack, network administrators know which subnet was attacked. Cybersecurity specialists can implement the principle of least privileges via subnet fragmentation to restrict access to important information only to authorized parties.
Simultaneously, it is easier to isolate the subnet from the whole network to prevent infection of other subnets or protect it via a firewall at the subnet entry. For example, ransomware relies on infecting as many connected devices as possible to encrypt them. With professional network segmentation, it will only infect the initial subnet without spreading to the whole network.
Common Subnet Sizes and Their Uses
There are several different subnet sizes optimized for more efficient data exchange. Organizations that have a lot of connected devices require a larger network to connect them all, so they need more host IDs. It results in a smaller number of subnets that have more space for devices.
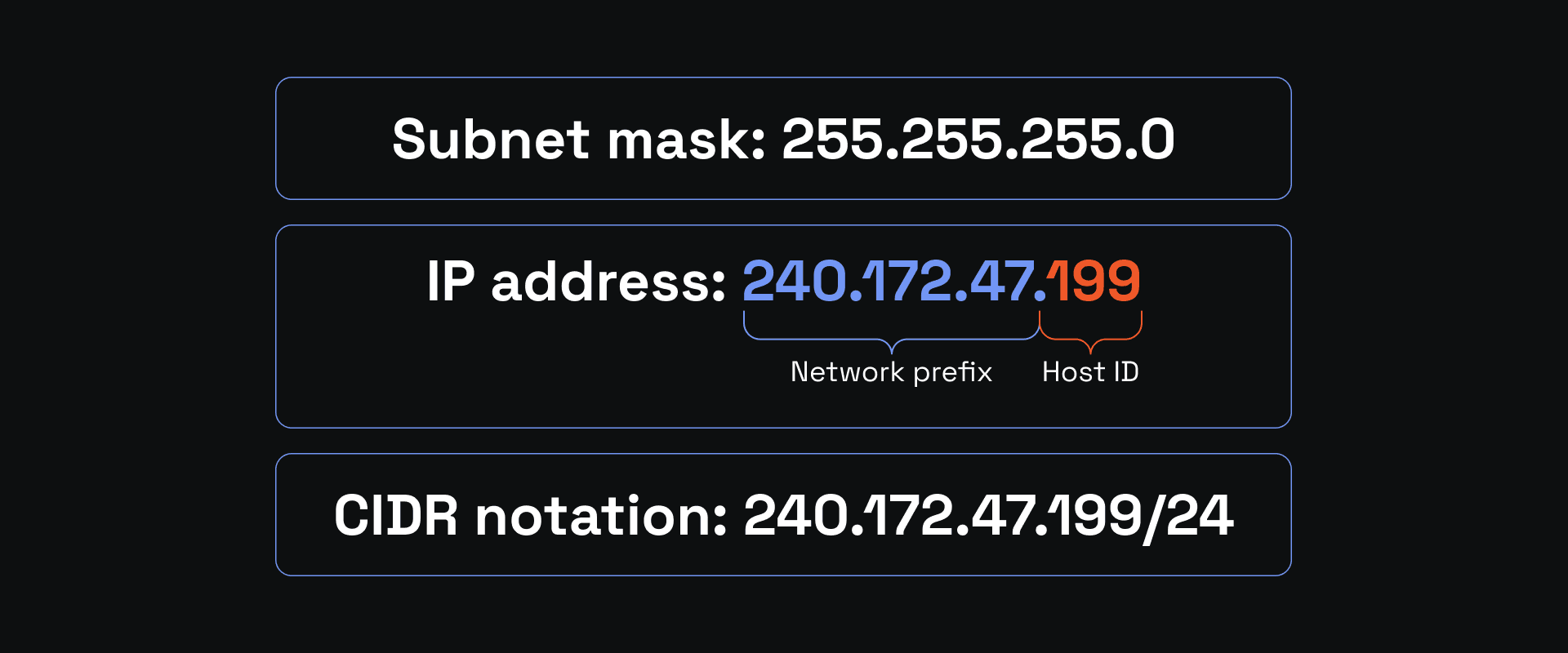
On the other hand, enterprises with only a few devices can operate on a smaller network. In this case, the network prefix can sustain many more subnets, but each subnet has fewer allocated IP addresses. At this point, let's take a closer look at IP addresses and how they store subnet IDs. Let's use the random 240.172.47.119 with the standard 255.255.255.0 subnet mask.
The subnet mask is used to derive the subnet ID. We'll show how to calculate subnet ID step by step at the end of this article, so jump to the last section if that's what you're looking for. A subnet mask indicates which part of the IP address is the network prefix and what's after points to the host ID.
Just like the IP address, the subnet mask is a 32-bit number. It consists of four 8-bit octets of 0 and 1, so, in binary, the standard 255.255.255.0 subnet mask looks like 11111111.11111111.11111111.00000000. The 1 represents which IP address part is reserved for the network prefix. In this example, 240.172.47.0 stands for the network identifier, while 0.119 for the host ID on the target subnet.
Now, we can understand the different network size types. For this, we will use the Classless Inter-Domain Routing (CIDR) notation, which is an organized way to visualize network size. Getting back to our example, the CIDR notation, with a standard 255.255.255.0 mask, would look like 240.172.47.199/24
The section after the / indicates how many 1 are included in the mask, and it shows what portion of the IP is reserved for the subnet ID. So, this CIDR notation shows that the first three octets stand for the network part, while the last octet is the host ID.
Subnet network sizes are often written in the CIDR notation for a more organized visual representation. So, if you have the /24 at the end, it means that the network ID can be divided from 3 eight-bit octets, while the host ID has only one octet.
In other words, it's a small network that can have up to 254 host addresses because the last octet stores 2^8 values, which equals 256. Because the first and the last addresses are always reserved for the network and broadcast addresses, the end result is 254 available host IDs. This subnet size is generally used for small networks, like a home network.
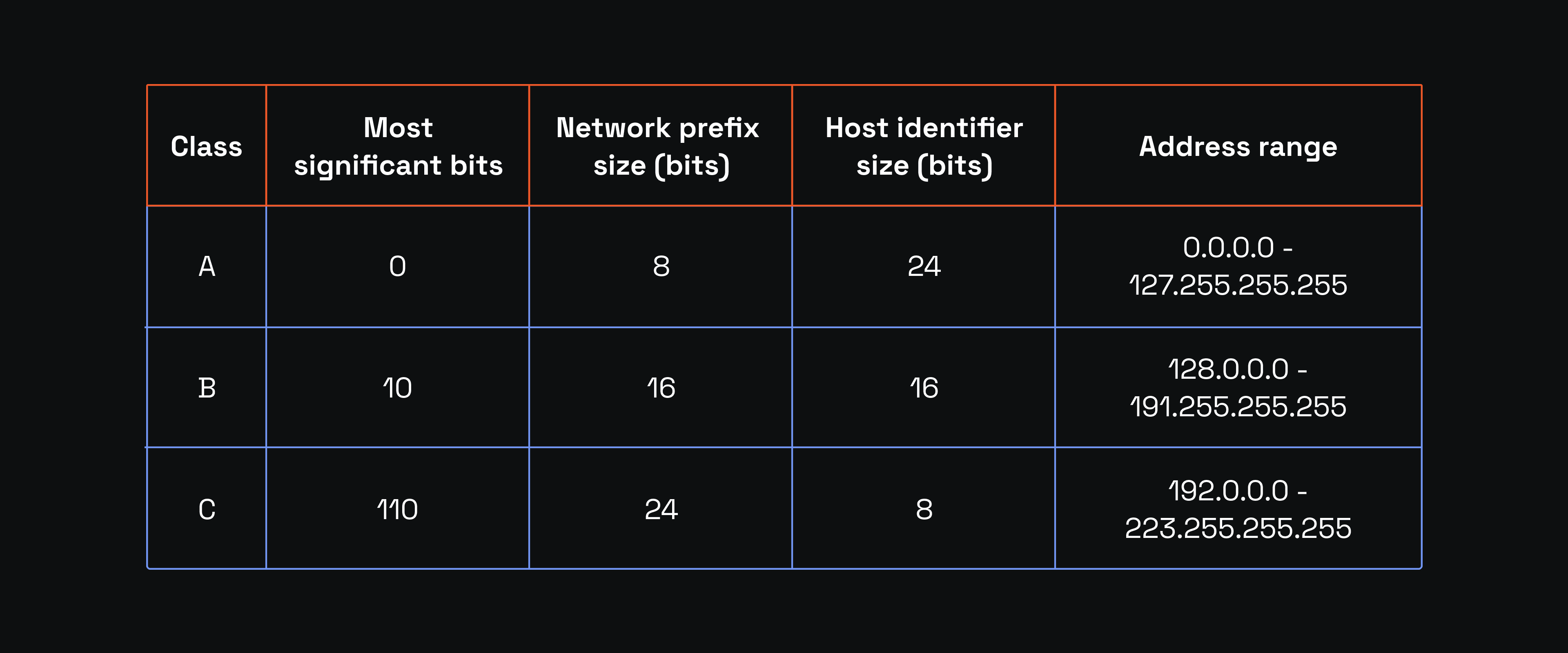
Suppose the subnet mask is 255.0.0.0. Then, our subnet ID in CIDR notation would be 240.172.47.199/8 because the network prefix consists of only one octet. It allows having 16.777.214 host IDs because you can have 2^24 IP addresses, subtracting 2 for network and broadcast addresses. It creates a single massive network with thousands of connected devices.
For easier representation, you can also use the class A, B, and C subnet CIDR notation (the D and E classes are rarely used).
Class A
Class A uses the 255.0.0.0 mask, and the first bit of the first octet is always 0. It is a massive network with a huge number of host IDs.
Class B
Class B uses the 255.255.0.0 mask, and the first octet always starts in 10 to form a medium-sized network.
Class C
Class C is 255.255.255.0, the first octet beginning in 110, which represents small networks with limited devices.
Subnet ID vs. Host ID
The more you go into computer networking, the more complex it becomes. Let's repeat the most important part of the article.
The IP address consists of two parts: the network prefix and the host ID. The network number indicates which subnet the host belongs to, while the host number shows the actual place of the device on a specific network. Remember the worldwide postal service example? The network details would reveal the country and the city (subnet), and the host information the exact delivery address (street and house number).
The size of each part depends on the subnet mask ID, which the network administrator sets. Most home networks have the mask of 255.255.255.0. The 255 is a digital representation of the 11111111 binary statement, and the number of 1 shows the network address segment size in the IP address. The image below summarizes this logic.
How to Calculate a Subnet ID
Whether you're a cybersecurity student or a business network administrator, you will often calculate a subnet ID. It allows segmenting large networks into smaller, more manageable parts, optimizing data routing protocols, and establishing functional cybersecurity controls. Here's how to do it from scratch using the IP address 240.172.47.199 example with a 255.255.255.0 mask.
Convert the IP address to binary. The result is
11110000.10101100.101111.11000111
Convert the mask to binary.
11111111.11111111.11111111.00000000
The conversion uses the bitwise operation because it works on a binary string. It uses the bitwise AND function to derive the subnet ID, which means that the outcome of 1 will be only when both IP and mask values are 1. Let's put them beneath each other for a better view.
11110000.10101100.101111.11000111
11111111.11111111.11111111.00000000
So the resulting subnet ID is:
11110000.10101100.101111.00000000 or 240.172.47.0. Because the default mask uses the first 3 octets for the network, the conversion correctly separates it from the host ID. In CIDR notation, the subnet ID would be 240.172.47.199/24.
Final Words
At first glance, separating the network address part from the target recipient may seem complex. Keep in mind that different subnet masks result in IP addresses for smaller or larger networks, and knowing which IP address portion belongs to the host or network is essential.
Simultaneously, remember that larger networks are much harder to maintain. Even though a larger network with thousands of available connections may sound tempting, it denies the segmentation logic. Generally, you aim to fragment an extensive IP network into smaller parts to optimize data transfers via routers and secure the perimeter from unauthorized actions.